- Can you reverse proxy SSH?
- Is Apache httpd a reverse proxy?
- What is SSH reverse proxy?
- What is the best reverse proxy?
- Is load balancer same as reverse proxy?
- What is reverse proxy in VRA?
- How does SSL work with reverse proxy?
- How is reverse proxy configured?
- Can I use HTTP proxy for HTTPS?
- Does SSH support SOCKS5?
- Can reverse proxy be hacked?
- Is SOCKS5 SSH secure?
- Does reverse proxy terminate SSL?
- Is SSH SOCKS4 or SOCKS5?
- Is SOCKS5 faster than HTTP?
- Can I use IPv6 for SSH?
- Does reverse proxy hide IP?
- What is the best reverse proxy?
- Is reverse proxy a VPN?
Can you reverse proxy SSH?
Reverse SSH Tunneling enables you to access remote machines behind NAT. For instance, you can access your office from home. Therefore, Reverse SSH Tunneling is a technique that enables you to SSH your Linux-based system that doesn't have a public IP address.
Is Apache httpd a reverse proxy?
In addition to being a "basic" web server, and providing static and dynamic content to end-users, Apache httpd (as well as most other web servers) can also act as a reverse proxy server, also-known-as a "gateway" server.
What is SSH reverse proxy?
Reverse SSH tunneling or remote port forwarding helps you connect to a remote (and private) network without needing a public gateway. Contrary to how SSH works, where you establish a secure connection with a remote system and can receive and send data, in reverse SSH, the remote system connects with your local system.
What is the best reverse proxy?
Apache HTTP server. Following choice of Top 10 Best Reverse Proxy is Apache HTTP Server. Arguably the most popular web server in the world. In fact, it be configured to act as a reverse proxy.
Is load balancer same as reverse proxy?
A reverse proxy accepts a request from a client, forwards it to a server that can fulfill it, and returns the server's response to the client. A load balancer distributes incoming client requests among a group of servers, in each case returning the response from the selected server to the appropriate client.
What is reverse proxy in VRA?
Understanding Reverse Proxy ( haproxy ) On vRealize Automation Appliance we have multiple services running simultaneously. An Open-Source application called HA Proxy is used to provide a reverse proxy on port 443 , routing traffic to each service appropriately.
How does SSL work with reverse proxy?
An SSL terminating reverse proxy is simply a web server that is configured to accept encrypted https requests from clients, and to forward them as unencrypted http requests to another backend process, and to relay the unencrypted results from the backend process back to the client via the encrypted channel.
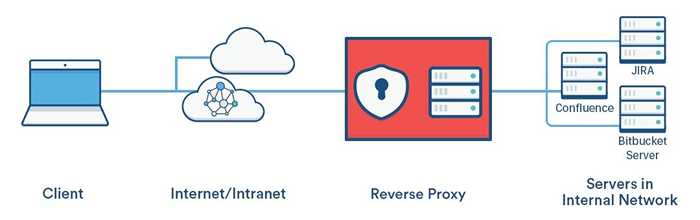
How is reverse proxy configured?
In a reverse proxy setup, the web server forwards the HTTP request it received from the browser client to the appropriate backend server. The HTML response from the backend server is sent back to the browser through the web server. Thus, the web server with reverse proxy hides the existence of backend servers.
Can I use HTTP proxy for HTTPS?
End-to-end security is achieved by establishing a secure channel between the client and the server after the proxy has connected to the server and confirmed the operation to the client. An HTTP proxy should not be used for HTTPS resources for purposes other than debugging or espionage.
Does SSH support SOCKS5?
Set up SOCKS5 SSH tunnel
You set up a SOCKS 5 tunnel in 2 essential steps. The first one is to build an SSH tunnel to a remote server. Once that's set up, you can configure your browser to connect to the local TCP port that the SSH client has exposed, which will then transport the data through the remote SSH server.
Can reverse proxy be hacked?
If a reverse proxy has a path-based rule which allows aggressive caching, an attacker can create such a path which falls into the rule but will be interpreted as a completely different path by a backend server.
Is SOCKS5 SSH secure?
A SOCKs5 proxy is more secure because it establishes a full TCP connection with authentication and uses the Secure Shell (SSH) encrypted tunneling method to relay the traffic.
Does reverse proxy terminate SSL?
An SSL terminating reverse proxy is simply a web server that is configured to accept encrypted https requests from clients, and to forward them as unencrypted http requests to another backend process, and to relay the unencrypted results from the backend process back to the client via the encrypted channel.
Is SSH SOCKS4 or SOCKS5?
SOCKS5 proxies use SSH (Secure Shell protocol) tunneling to access online anonymously. The SOCKS5 uses TCP and IPX (Internet Packet Exchange) to establish a connection between the client and the server.
Is SOCKS5 faster than HTTP?
A SOCKS5 proxy is faster than an HTTP proxy since it supports UDP connections. UDP is faster and more efficient than TCP.
Can I use IPv6 for SSH?
Configuring SSH for IPv6. By default, SSH is automatically enabled for IPv4 and IPv6 connections on a switch. Use the ip ssh command options to reconfigure the default SSH settings used in SSH authentication for IPv4 and IPv6 connections: TCP port number.
Does reverse proxy hide IP?
Businesses hide their web servers' IP addresses, and one of the ways is by using a reverse proxy. A reverse proxy receives a request from internet users, passes it to a web server that can fulfil it, and brings back the server's response to the user. This means that the real web server's IP address is never exposed.
What is the best reverse proxy?
Apache HTTP server. Following choice of Top 10 Best Reverse Proxy is Apache HTTP Server. Arguably the most popular web server in the world. In fact, it be configured to act as a reverse proxy.
Is reverse proxy a VPN?
Is VPN a forward proxy or reverse proxy? A VPN is a forward proxy. A reverse proxy is a type of proxy server that forwards requests to other servers on behalf of the client.
 Torgeek
Torgeek