- What is MITRE Matrix?
- What is the MITRE Shield framework?
- What is the difference between MITRE engage and shield?
- What is MITRE attack mapping?
- What are MITRE Att&ck matrix techniques?
- What is the purpose of MITRE?
- Is MITRE a threat model?
- Is MITRE ATT&ck a threat intelligence?
- How does privacy shield framework work?
- What are the 3 main matrices of the Mitre ATT&CK framework?
- What are the two types of Mitre?
- How many Mitre techniques are there?
- What does MITRE CVE stand for?
- How many MITRE Att&ck matrices are there?
- What is MITRE in cyber security?
- What is MITRE evaluation?
- Did MITRE create CVE?
- What does a CVE score of 10 mean?
- What is CVE in firewall?
What is MITRE Matrix?
The MITRE ATT&CK matrix contains a set of techniques used by adversaries to accomplish a specific objective. Those objectives are categorized as tactics in the ATT&CK Matrix. The objectives are presented linearly from the point of reconnaissance to the final goal of exfiltration or "impact".
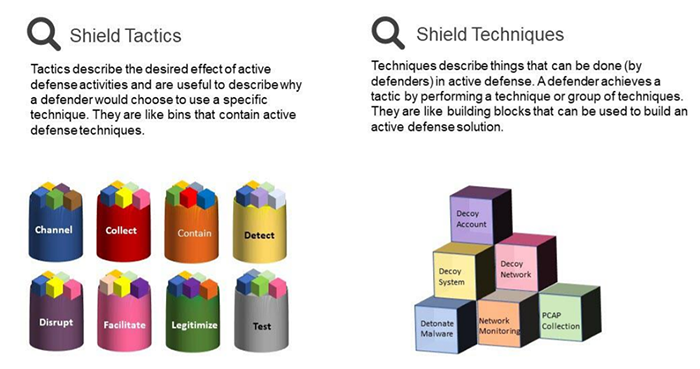
What is the MITRE Shield framework?
MITRE Shield is a knowledge base designed to give defenders tools that can be used to counter cyber adversaries. Shield includes a database of techniques a defender can use to mount an active defense. The knowledge base also describes a number of tactics common to defensive plans.
What is the difference between MITRE engage and shield?
While MITRE Shield was a technique-heavy and execution-focused framework, Engage adds the much-needed layers of planning and analysis by bookending deception techniques with activities that can help defenders define the scope of their active defense operations and use the threat intelligence gathered to inform threat ...
What is MITRE attack mapping?
MITRE ATT&CK - Mobile: Provides a model of adversarial tactics and techniques to operate within the Android and iOS platforms. ATT&CK for Mobile also contains a separate matrix of network-based effects, which are techniques that an adversary can employ without access to the mobile device itself.
What are MITRE Att&ck matrix techniques?
The MITRE ATT&CK Windows Matrix for Enterprise consists of 12 tactics: Initial Access, Execution, Persistence, Privilege Escalation, Defense Evasion, Credential Access, Discovery, Lateral Movement, Collection, Command and Control, Exfiltration and Impact.
What is the purpose of MITRE?
MITRE ATT&CK (Adversarial Tactics, Techniques and Common Knowledge) is a framework, set of data matrices, and assessment tool developed by MITRE Corporation to help organizations understand their security readiness and uncover vulnerabilities in their defenses.
Is MITRE a threat model?
The most popular threat modeling framework today is called the MITRE ATT&CK framework. This framework, provided by the MITRE Corporation, is structured based on common threat actor TTPs, offering a methodology for security risk management of those TTPs in the security environment.
Is MITRE ATT&ck a threat intelligence?
MITRE ATT&CK as Part of Nozomi Networks Threat Intelligence
Threat Intelligence delivers ongoing OT (Operational Technology) and IoT threat and vulnerability intelligence, which is correlated with broader environmental behavior to deliver vast security and operational insight.
How does privacy shield framework work?
Privacy Shield is an agreement between the EU and US allowing for the transfer of personal data from the EU to US. The GDPR has specific requirements regarding the transfer of data out of the EU. One of these requirements is that the transfer must only happen to countries deemed as having adequate data protection laws.
What are the 3 main matrices of the Mitre ATT&CK framework?
The Enterprise ATT&CK matrix is a superset of the Windows, MacOS, and Linux matrices.
What are the two types of Mitre?
There are three types of mitre saws: sliding, compound and sliding compound.
How many Mitre techniques are there?
There are currently 185 techniques and 367 sub-techniques in the Enterprise ATT&CK matrix, and Mitre continuously adds more. Each technique has a four-digit code—for example, Abuse Elevation Control Mechanism is T1548.
What does MITRE CVE stand for?
Common Vulnerabilities and Exposures (CVE) is a list of publicly disclosed information security vulnerabilities and exposures. CVE was launched in 1999 by the MITRE corporation to identify and categorize vulnerabilities in software and firmware.
How many MITRE Att&ck matrices are there?
The MITRE ATT&CK framework revolves around a knowledge base of cyber adversary tactics, techniques, and procedures (TTPs). The knowledge base is organized in the form of an attack matrix (or, ATT&CK matrix), currently consisting of 14 columns with varying numbers of rows under each.
What is MITRE in cyber security?
The MITRE ATTACK Framework is a curated knowledge base that tracks cyber adversary tactics and techniques used by threat actors across the entire attack lifecycle. The framework is meant to be more than a collection of data: it is intended to be used as a tool to strengthen an organization's security posture.
What is MITRE evaluation?
About MITRE Engenuity ATT&CK® Evaluations
ATT&CK® Evaluations (Evals) is built on the backbone of MITRE's objective insight and conflict-free perspective. Cybersecurity vendors turn to the Evals program to improve their offerings and to provide defenders with insights into their product's capabilities and performance.
Did MITRE create CVE?
The CVE List was launched by the MITRE Corporation as a community effort in 1999. The U.S. National Vulnerability Database (NVD) was launched by the National Institute of Standards and Technology (NIST) in 2005.
What does a CVE score of 10 mean?
Scores range from 0 to 10, with 10 being the most severe. While many utilize only the CVSS Base score for determining severity, temporal and environmental scores also exist, to factor in availability of mitigations and how widespread vulnerable systems are within an organization, respectively.
What is CVE in firewall?
CVE stands for Common Vulnerabilities and Exposures. CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability.
 Torgeek
Torgeek