- What is the purpose of a Tor introduction point?
- What is Tor Rendezvous point?
- When was Tor introduced?
- What is the concept of Tor?
- Is Tor better than a VPN?
- Is Tor made by the CIA?
- Which bridge is good in Tor?
- What is a Tor exit relay?
- How was Tor discovered?
- Why is it called Tor?
- Who created the dark web and why?
- What is the importance of ToR?
- What does ToR stand for in project?
- What is the most important strength of ToR?
- What are the objectives of terms of reference?
- How does Tor work simple?
- Do hackers use Tor?
- Does Tor use a VPN?
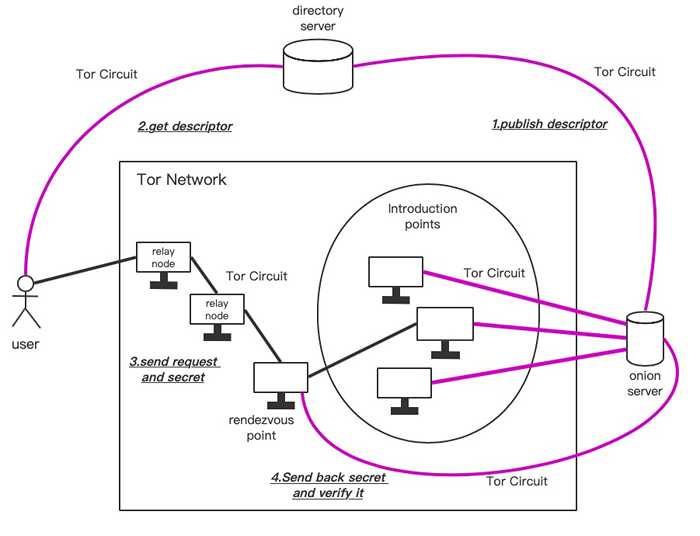
What is the purpose of a Tor introduction point?
The introduction point sends the message to the server and the server can choose to accept it or do nothing. If the server accepts the message it will then create a circuit to the rendezvous point.
What is Tor Rendezvous point?
Rendezvous Point -- A Tor node to which clients and servers. connect and which relays traffic between them.
When was Tor introduced?
The alpha version of Tor, developed by Syverson and computer scientists Roger Dingledine and Nick Mathewson and then called The Onion Routing project (which was later given the acronym "Tor"), was launched on 20 September 2002. The first public release occurred a year later.
What is the concept of Tor?
Tor—short for the Onion Routing project—is an open-source privacy network that enables anonymous web browsing. The worldwide Tor computer network uses secure, encrypted protocols to ensure that users' online privacy is protected.
Is Tor better than a VPN?
Tor is better than a VPN for the following: Anonymously accessing the web – It's almost impossible to trace a Tor connection back to the original user. You can safely visit a website without leaving any identifying evidence behind, both on your device and on the website's server.
Is Tor made by the CIA?
Since then, the Tor Project has been funded by Princeton University, the US State Department, Mozilla, the National Science Foundation, and DARPA, among others. But it is not, and never was, a CIA project, in whole or in part.
Which bridge is good in Tor?
A Tor bridge is basically a guard node that isn't listed in the public directory, making it harder for censors to block. Obfs4 and meek-azure are the most commonly used bridges, but Snowflake bridges might become more popular in the near future.
What is a Tor exit relay?
An exit relay is the final relay that Tor traffic passes through before it reaches its destination. Exit relays advertise their presence to the entire Tor network, so they can be used by any Tor users.
How was Tor discovered?
In the early 1990s, the biochemist Michael N. Hall discovered the protein «TOR» in yeast cells. It later emerged that TOR centrally controls cell growth in many organisms and is implicated in many diseases such as diabetes and cancer.
Why is it called Tor?
Tor was originally developed for the U.S. Navy in an effort to protect government communications. The name of the software originated as an acronym for the The Onion Router, but Tor is now the official name of the program.
Who created the dark web and why?
The dark web is known to have begun in 2000 with the release of Freenet, the thesis project of University of Edinburgh student Ian Clarke, who set out to create a "Distributed Decentralised Information Storage and Retrieval System." Clarke aimed to create a new way to anonymously communicate and share files online.
What is the importance of ToR?
Terms of reference are important to set expectations and constrain scope. A terms of reference (ToR) is a document which articulates the scope of work for a taskforce and how the people identified in the ToR will work together in the pursuit of a shared goal.
What does ToR stand for in project?
The terms of reference (ToR) is a key document to support the governance arrangements of the project. The ToR for the project board would usually be defined at project brief stage.
What is the most important strength of ToR?
What is the most important strength of TOR? Its involvement of line personnel in the analysis. Name five widely applicable hazard prevention strategies.
What are the objectives of terms of reference?
Terms of Reference (ToR) can set out the working arrangements for a network and can list vital information about the network, such as its purpose, chair and membership, meeting schedule, level of administrative support, and dispute resolution processes.
How does Tor work simple?
Tor works by sending your traffic through three random servers (also known as relays) in the Tor network. The last relay in the circuit (the “exit relay”) then sends the traffic out onto the public Internet. The image above illustrates a user browsing to different websites over Tor.
Do hackers use Tor?
The usage of Tor could increase the level of anonymity, but a hacker can always track users from their Bitcoin payments. “We demonstrate that the use of Tor does not rule out the attack as Tor connections can be prohibited for the entire network.
Does Tor use a VPN?
No, it isn't. Tor is a browser and only encrypts the data transmitting through the browser. A VPN is specific privacy protection software and encrypts all data coming out of a device, whether it comes from a browser or an app. The key difference between a VPN and Tor are their operation methods.
 Torgeek
Torgeek