- What common relay attack is used against SMB services?
- Which vulnerability does SMB Relay exploit?
- How does SMB relay attack work?
- How is SMB exploited?
- Why is SMB so vulnerable?
- What is more secure than SMB?
- Can a hacker still damage a network using SMB?
- Can ransomware spread through SMB?
- Should I block SMB?
- Can I disable SMB?
- Does SMB work over WiFi?
- What is the most common attack on network servers?
- Which of the following ports are associated with SMB attacks?
- Which algorithm is used by SMB for encryption?
What common relay attack is used against SMB services?
SMB Relay Attack is a type of attack which relies on NTLM Version 2 authentication that is normally used in most companies. Unfortunately, when we are listening to what is going on in the network, we're able to capture a certain part of the traffic related to the authentication and also relay it to the other servers.
Which vulnerability does SMB Relay exploit?
The SMB Relay attack abuses the NTLM challenge-response protocol. Commonly, all SMB sessions used the NTML protocol for encryption and authentication purposes (i.e. NTLM over SMB).
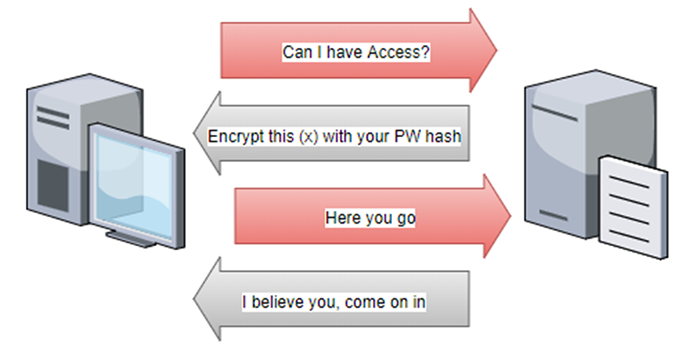
How does SMB relay attack work?
A SMB relay attack is where an attacker captures a users NTLM hash and relays its to another machine on the network. Masquerading as the user and authenticating against SMB to gain shell or file access.
How is SMB exploited?
Vulnerabilities may be exploited directly through exposed SMB ports, in conjunction with other vulnerabilities that enable an attacker to access internal SMB services, or through phishing attempts containing malware that targets SMB.
Why is SMB so vulnerable?
Why is it a risk? Version 1.0 of SMB contains a bug that can be used to take over control of a remote computer. The US National Security Agency (NSA) developed an exploit (called “EternalBlue”) for this vulnerability which was subsequently leaked.
What is more secure than SMB?
However, NFS is better with encryption. In the case of random writing, NFS is better than SMB in both plain text and encryption. If you use rsync for file transfer, NFS is a better choice in plain text and encryption.
Can a hacker still damage a network using SMB?
SMBv1 has a number of vulnerabilities that allow for remote code execution on the target machine. Even though most of them have a patch available and SMBv1 is no longer installed by default as of Windows Server 2016, hackers are still exploiting this protocol to launch devastating attacks.
Can ransomware spread through SMB?
Some of the most devastating ransomware and Trojan malware variants depend on vulnerabilities in the Windows Server Message Block (SMB) to propagate through an organization's network.
Should I block SMB?
You must not globally block inbound SMB traffic to domain controllers or file servers. However, you can restrict access to them from trusted IP ranges and devices to lower their attack surface.
Can I disable SMB?
Under Control Panel Home, select Turn Windows features on or off to open the Windows Features box. In the Windows Features box, scroll down the list, clear the check box for SMB 1.0/CIFS File Sharing Support and select OK. After Windows applies the change, on the confirmation page, select Restart now.
Does SMB work over WiFi?
If the computer was powered on (booted or resumed) with both connections on, SMB works using wired network, as it should be. However, when only WiFi was used for some time and then ethernet cable is connected, SMB still use WiFi. It is needed to turn off wireless connection to achieve faster wired transfer.
What is the most common attack on network servers?
Malware is the most common type of cyberattack, mostly because this term encompasses many subsets such as ransomware, trojans, spyware, viruses, worms, keyloggers, bots, cryptojacking, and any other type of malware attack that leverages software in a malicious way.
Which of the following ports are associated with SMB attacks?
SMB ports are generally port numbers 139 and 445. Port 139 is used by SMB dialects that communicate over NetBIOS. It operates as an application layer network protocol for device communication in Windows operating systems over a network.
Which algorithm is used by SMB for encryption?
SMB encryption uses AES-128-GCM or AES-128-CCM (with the GCM variant being chosen if the client supports SMB 3.1. 1) as its encryption algorithm, and also provides data integrity with signing using SMB Kerberos session keys.
 Torgeek
Torgeek