Attack
Bitcoin tor attack
Does Bitcoin use Tor?What is a Tor attack?Is 51% attack on Bitcoin possible?How does a 51% attack work? Does Bitcoin use Tor?Tor provides anonymous ...
Dos attack on router log
What is DoS attack in my router log?Can your router be DDoS?What happens when someone DDoS your router? What is DoS attack in my router log?A DDoS (...
Types of server-side attacks
Web Server Attacks types:DOS attack: ... Website Defacement: ... Directory Traversal: ... Misconfiguration attacks: ... Phishing Attack: ... Informati...
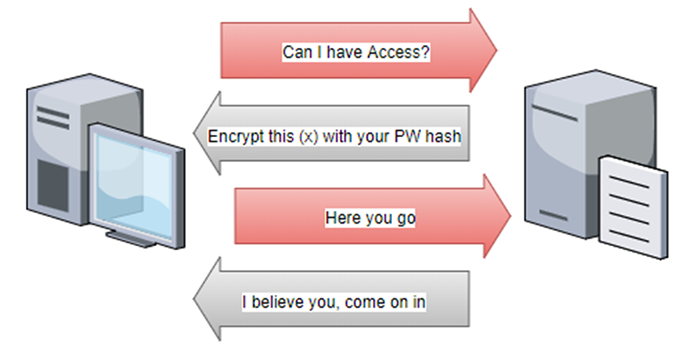
How to prevent smb relay attack
What common relay attack is used against SMB services?Which vulnerability does SMB Relay exploit?How does SMB relay attack work?How is SMB exploited?...
Ssl stripping attack example
What are examples of SSL stripping?What type of attack is an SSL stripping?What does SSL strip do?Is SSL stripping an on Path attack?Is SSL stripping...
Ssl stripping attack tutorial
How does SSL stripping attack work?What type of attack is an SSL stripping?What are the commands for SSLStrip?What is an SSL strip MitM attack?What i...
XSS example
What is XSS attack with example?What is a real example of XSS?How XSS attack is executed?What are common XSS attacks?How do hackers use XSS?Which is ...
Sybil attack blockchain
A Sybil attack uses a single node to operate many active fake identities (or Sybil identities) simultaneously, within a peer-to-peer network. This typ...
Sybil attack ethereum
What is a Sybil attack Crypto?What type of attack is Sybil attack?Is Sybil attack possible on Bitcoin?How do you detect a Sybil attack?Is Sybil attac...
 Torgeek
Torgeek